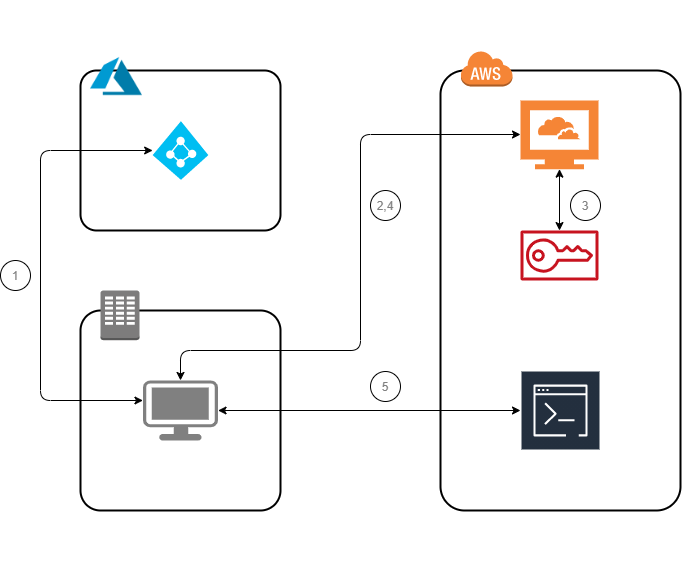
AWS CLI AssumeRoleWithSAML using STS Credentials
Description
AssumeRoleWithSAML returns a set of temporary security credentials for users who have been authenticated via a SAML authentication response. This operation provides a mechanism for tying an enterprise identity store or directory to role-based AWS access without user-specific credentials or configuration.
Preconfiguration
Another configuration must be prepared before you will continue. Click button on the right to jump into
IAM Federation with AzureAD
Configs (AzureAD)
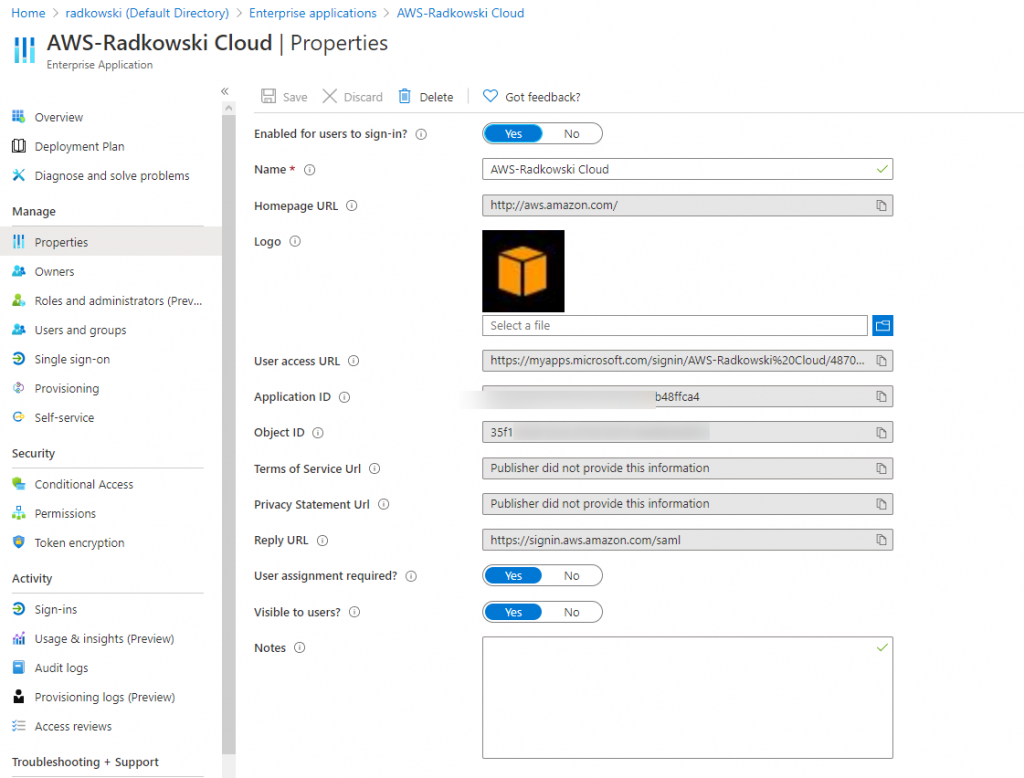
1.Input data
Log into Azure Console, select EnterpriseApplication, click properties and save ApplicationID
Configs (Linux console)
2. CLI configuration
To start using saml2aws, follow next steps:
- install and check awscli
- download and untar saml2aws app
[angelos@diomedes ~]$ CURRENT_VERSION=2.26.1
[angelos@diomedes ~]wget https://github.com/Versent/saml2aws/releases/download/v{CURRENT_VERSION}/saml2aws_${CURRENT_VERSION}_linux_amd64.tar.gz
[angelos@diomedes ~]$ tar zxvf saml2aws_2.26.1_linux_amd64.tar.gz
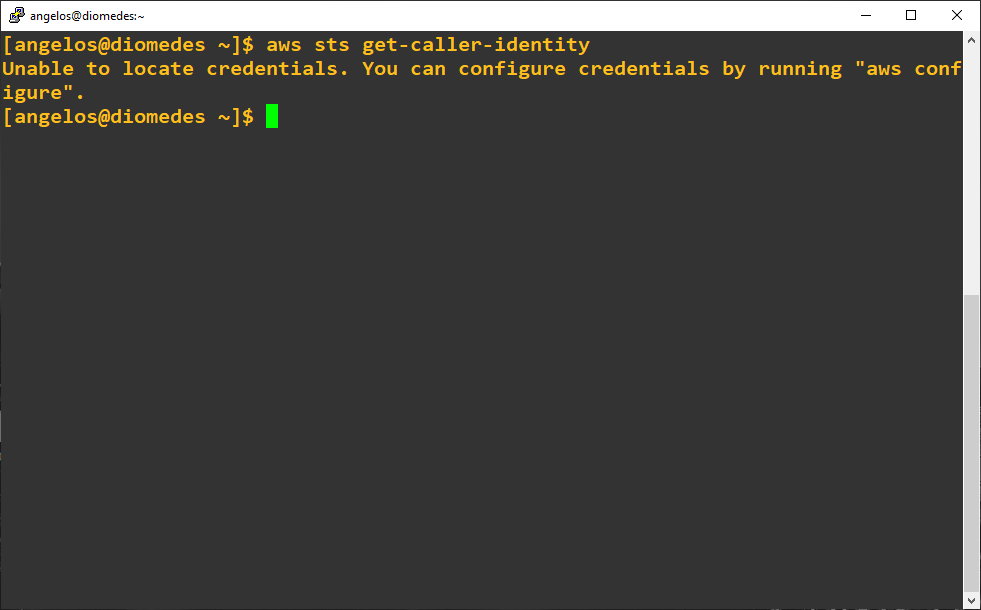
- confirm that you are not authenticated - no old aws credentials are configured
[angelos@diomedes ~]$ aws sts get-caller-identity
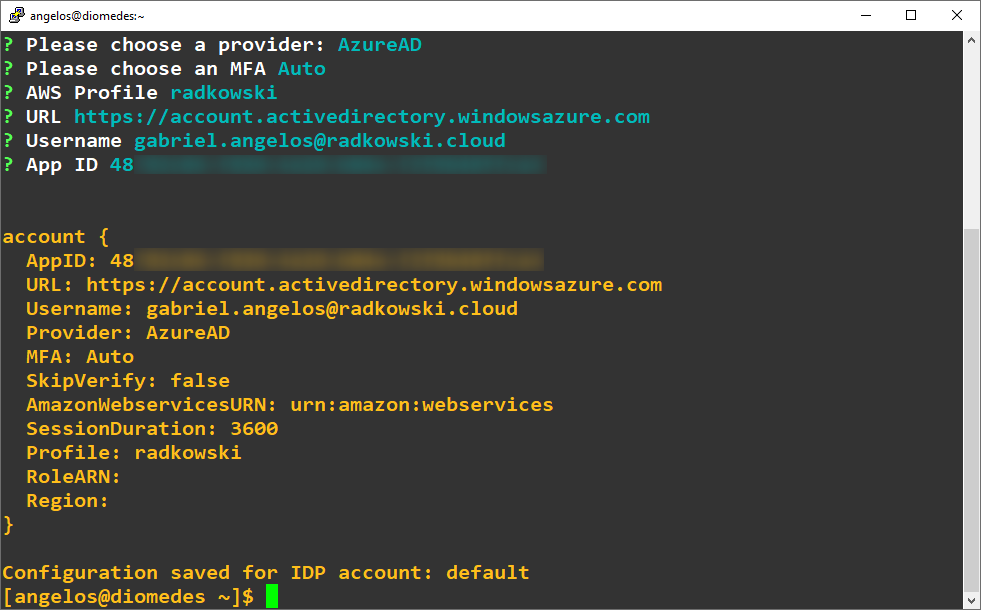
3. SAML2AWS configuration
To configure saml2aws, execute following command:
[angelos@diomedes ~]$ ./saml2aws configure
Provide all data, including ApplicationAID captured in step #1
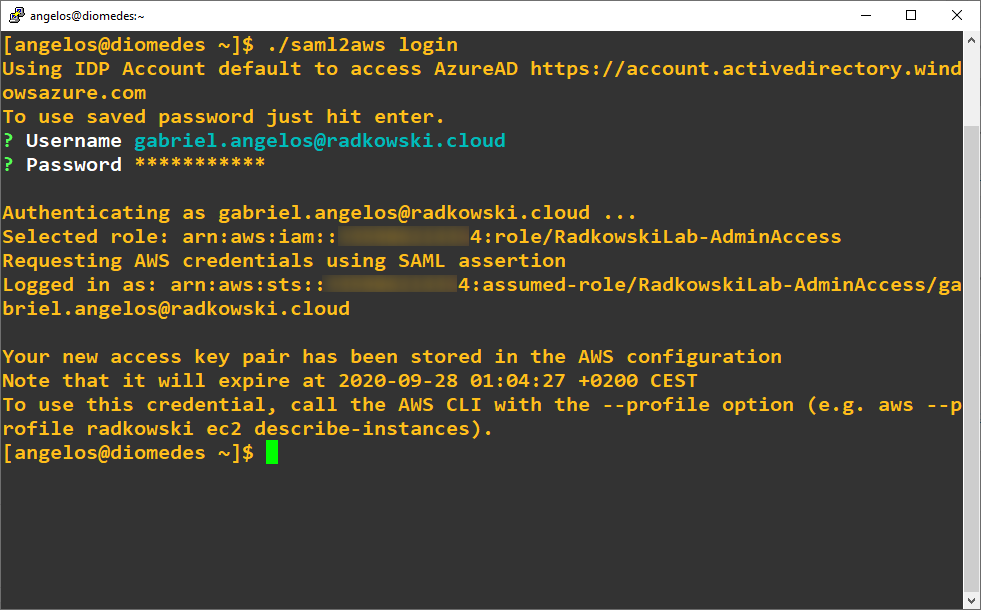
4. SAML2AWS login
To log into AWS, execute following command:
[angelos@diomedes ~]$ ./saml2aws login
Test Area
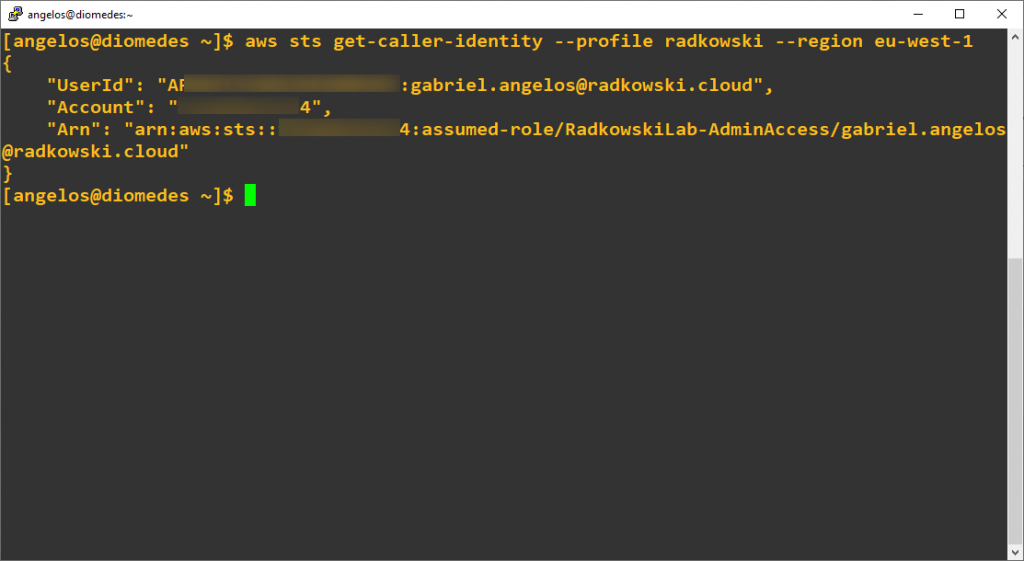
5. SAML2AWS STS test
Confirm, you have been successfully authenticated:
[angelos@diomedes ~]$ aws sts get-caller-identity --profile radkowski --region eu-west-1
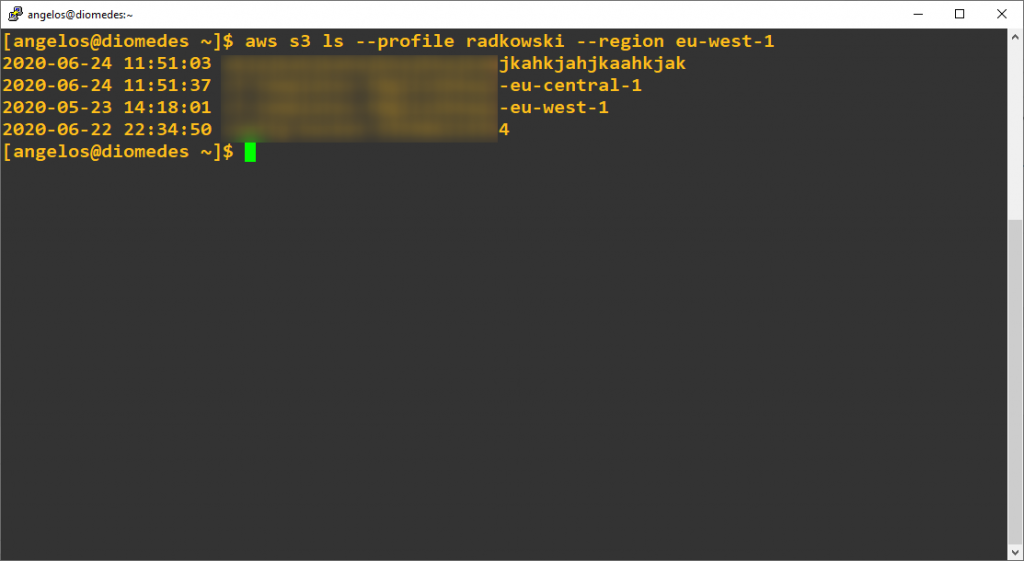
5. SAML2AWS S3 test
Execute following command to confirm if you have access to AWS resources (following command lists all S3 buckets)
[angelos@diomedes ~]$ aws s3 ls --profile radkowski --region eu-west-1