AWS STS-AssumeRole
Description
STS assumeRole returns a set of temporary security credentials that can be used to access AWS resources. These temporary credentials consist of an access key ID, a secret access key, and a security token. The credentials created by AssumeRolecan be used to make API calls to any AWS service with the following exception: it cannot call the AWS STS GetFederationToken or GetSessionToken API operations.
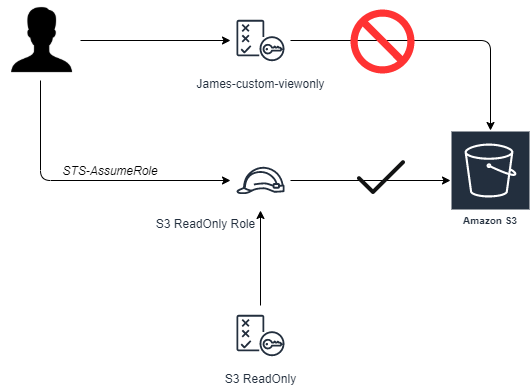
Lab Schema
Config
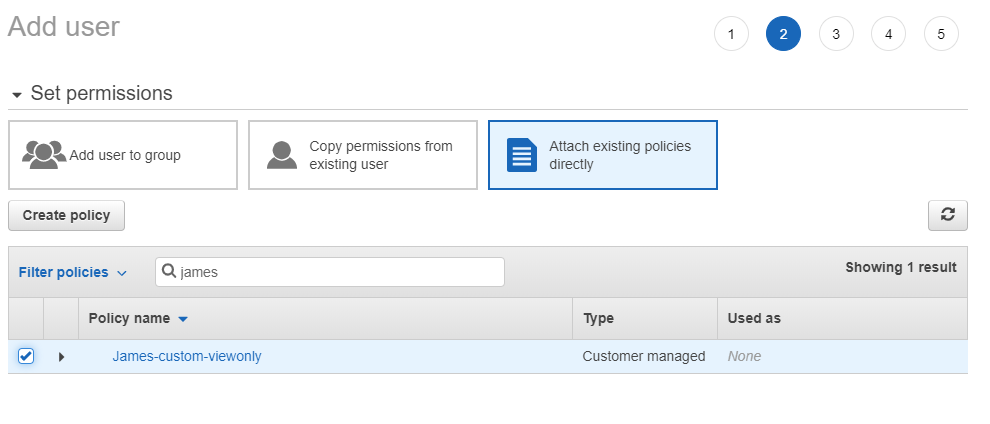
1. Create James-custom-viewonly policy
Log on to console with admin rights, and use IAM to create a new policy based on listing in the right panel. This policy has been created using AWS predefined VioewOnlyAccess role by removing S3-related actions.
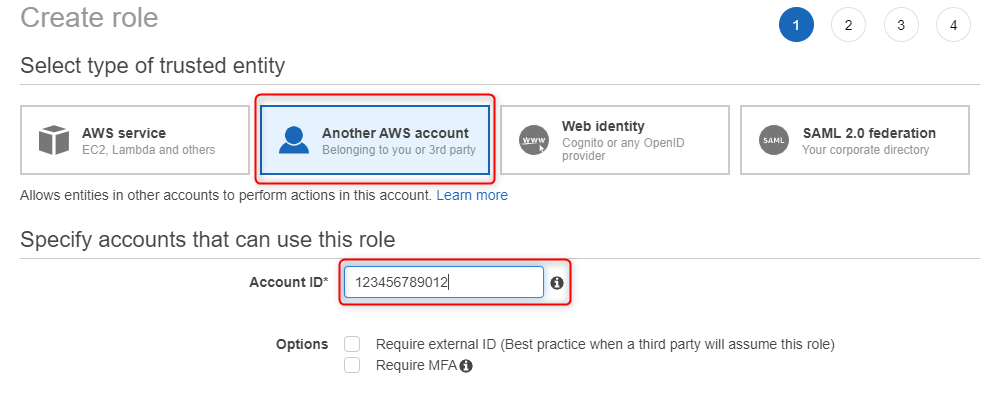
2. Create James-custom-S3 role - define trusted identity
Log on to console with admin rights, and use IAM to create a new role. Select Another AWS Account as a type of trusted identity and enter Account ID you are currently working on.
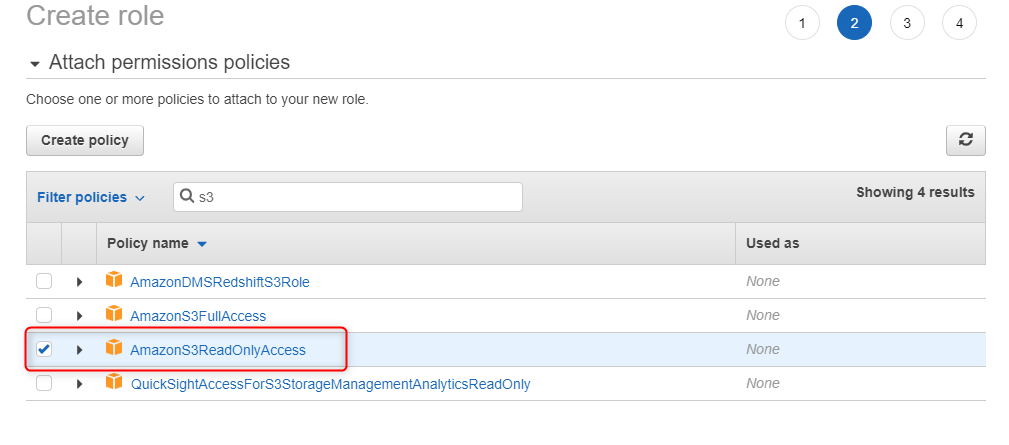
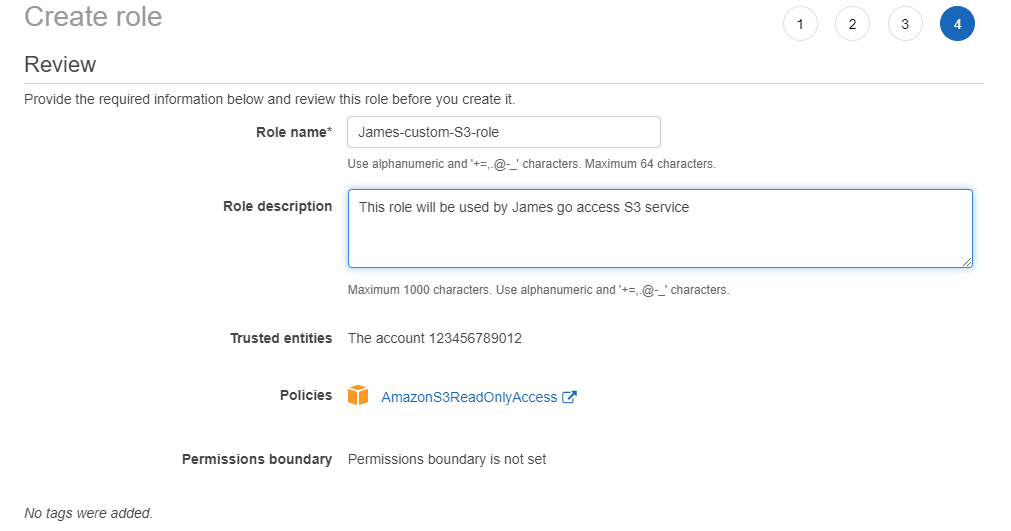
4. Create James-custom-S3 role - review
Enter role name and description, then press Create role button.
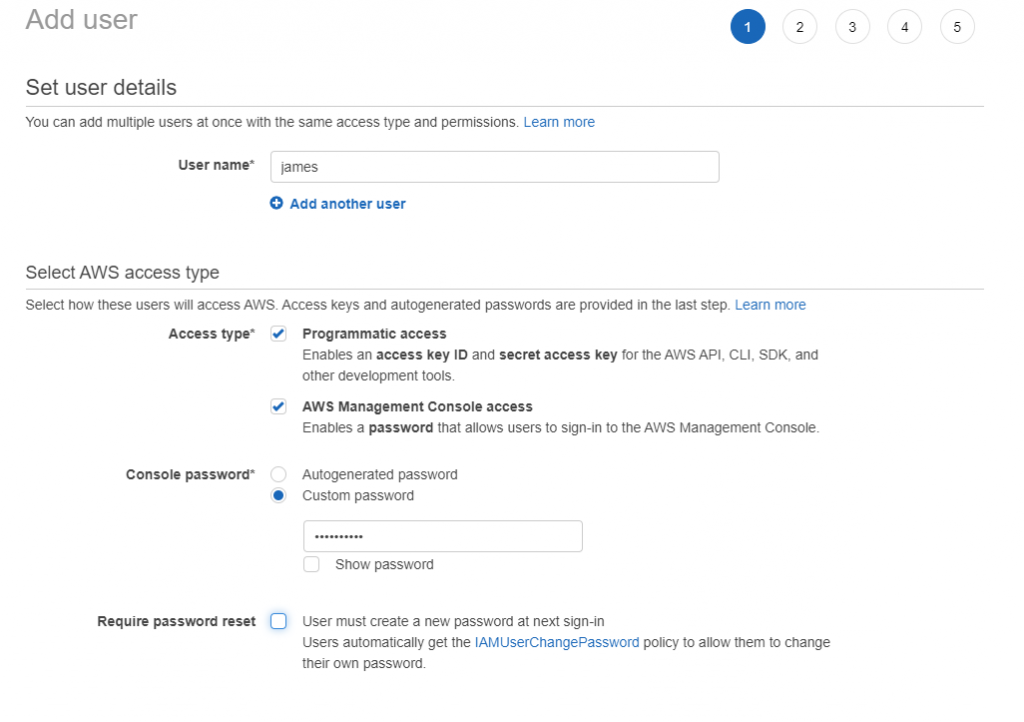
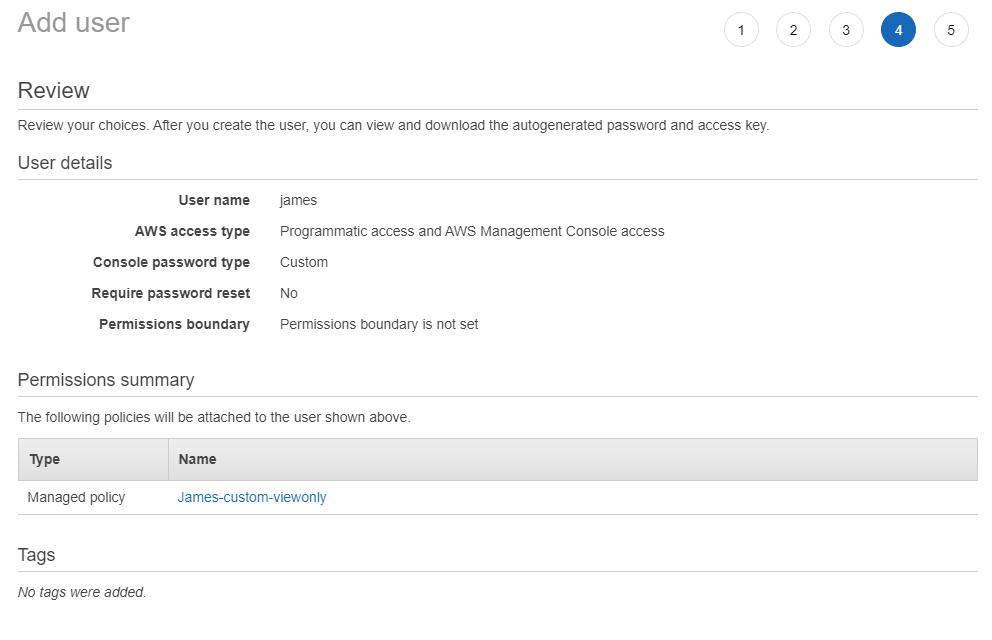
5. Create user James - define access type
Using IAM create user James and with access both to Management Console and via Programmatic access
6. Create user James - permissions set
Attach to user James previously created policy: James-custom-viewonly.
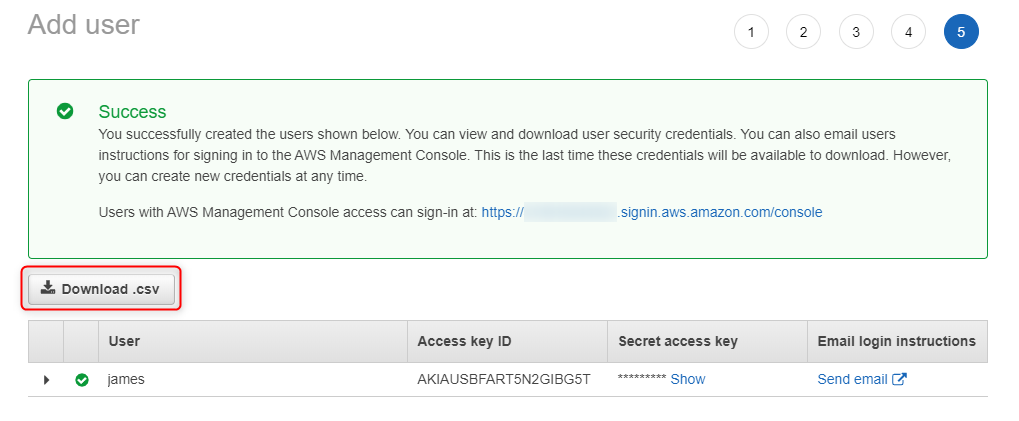
8. Create user James - download programmatic access credentials
Using Download.csv button, download programmatic access credentials (it can be done only once). Additionaly, safe AWS Management Console URL whch wil be used to log in user James into AWS
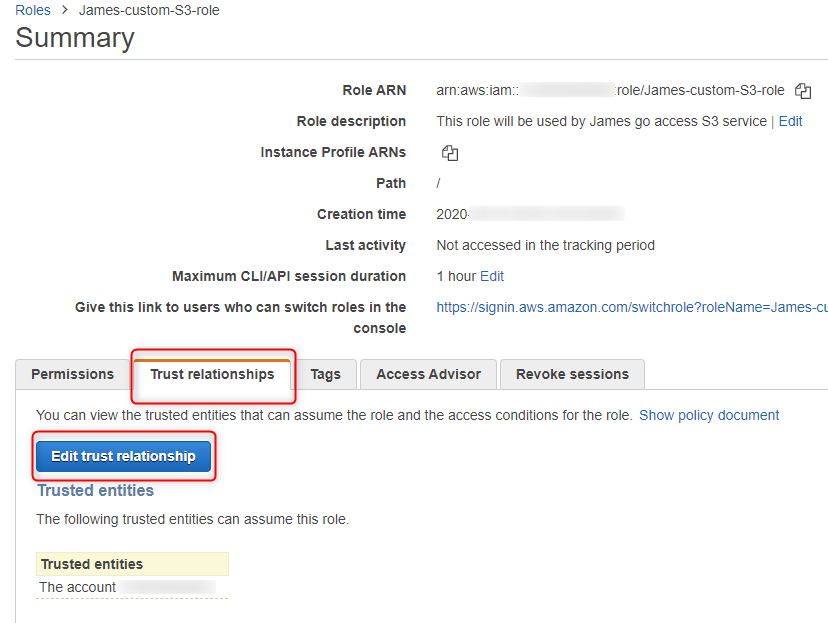
10. Update role trust selationship
Using IAM, select James-custom-S3-role and press Edit trust relationship (it can be found in Trust relationships tab)
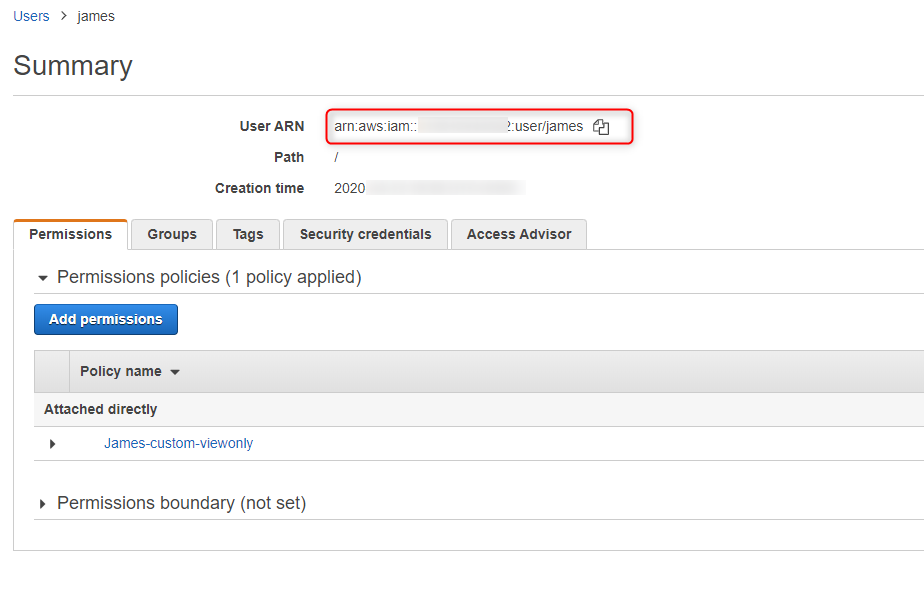
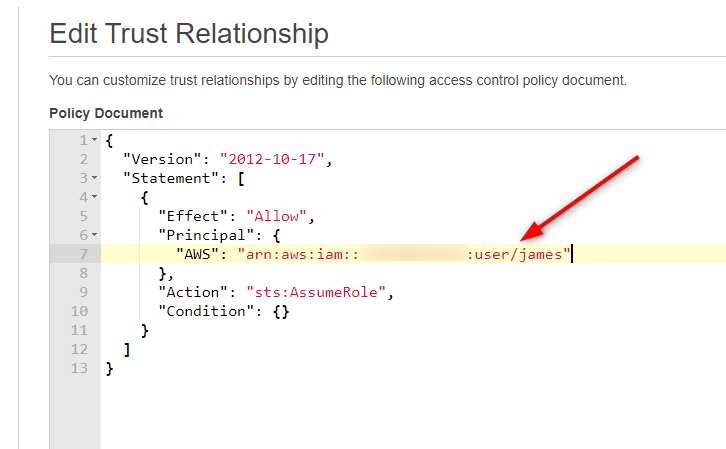
11. Edit trust relationship
Edit line 7 by adding user ARN (capture in step 9)
Test Area - AWS Console
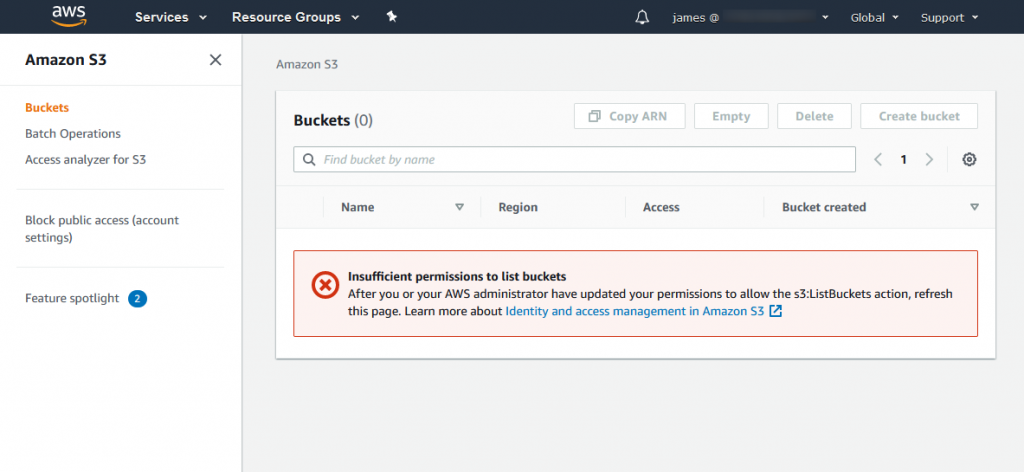
12. Check James access to S3
Using URL captured in step 8, log in to AWS console as user James. Select S3 service - you should get error (Insufficient permissions). It is expected, as James policy doesn't allow to access S3 (implict deny)
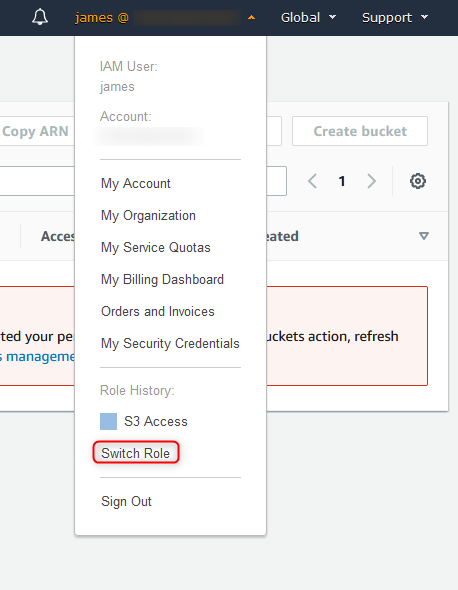
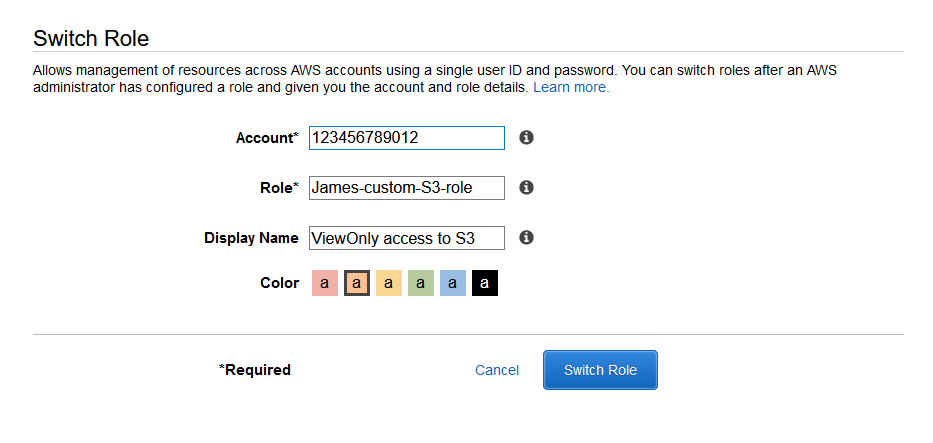
14. Switch role (#2)
Enter account ID and role name (based on previous configuration). You can also enter friendly name and color.
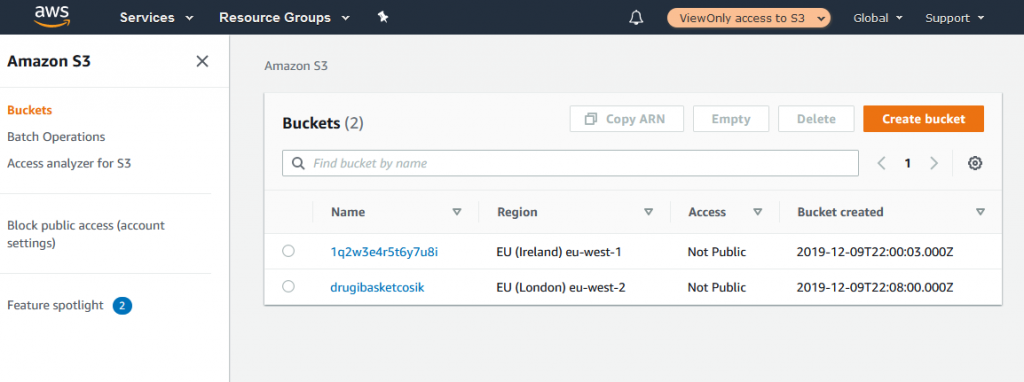
15. Review access
Once role is assumed, access to S3 service is granted (based on Allow policy configured in step 3).
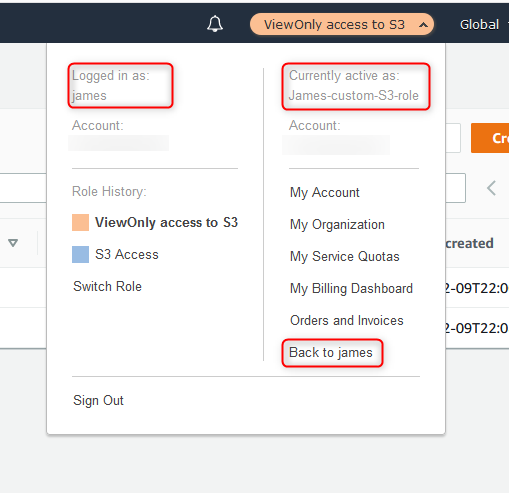
16. Assumed role details
Once role is assumed, user tab will change into name and color defined in step 14. Once clicked, it shows login details such as: logged in as, currently active as.
To come back to standard user account, press Back to james.
Test Area - AWS CLI
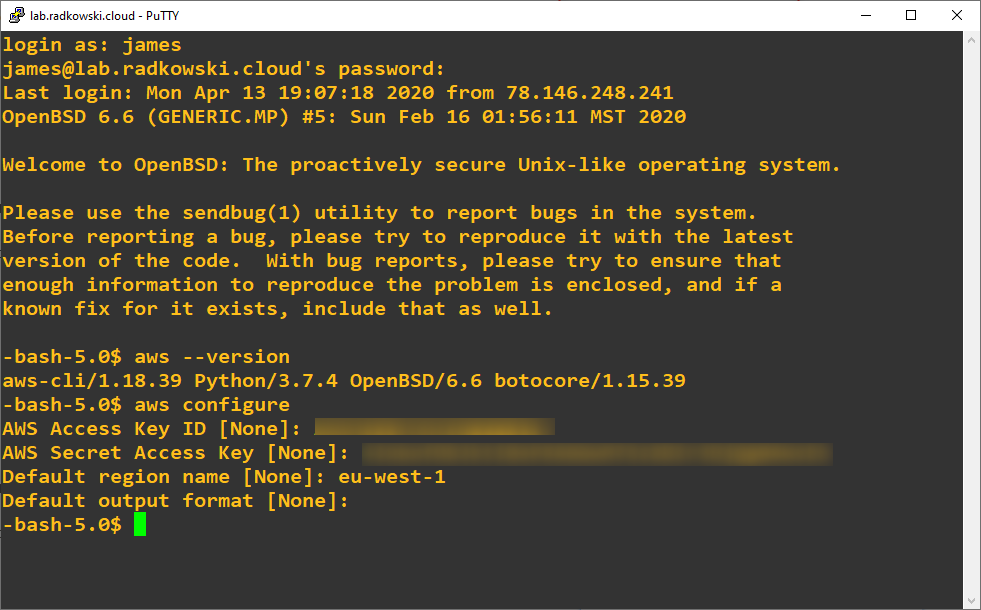
17. Configure AWSCLI
To assume role from CLI, install and configure AWS CLI. Use credentials collected in step 8 (it will grant access to AWS as user James)
18. CLI access as James
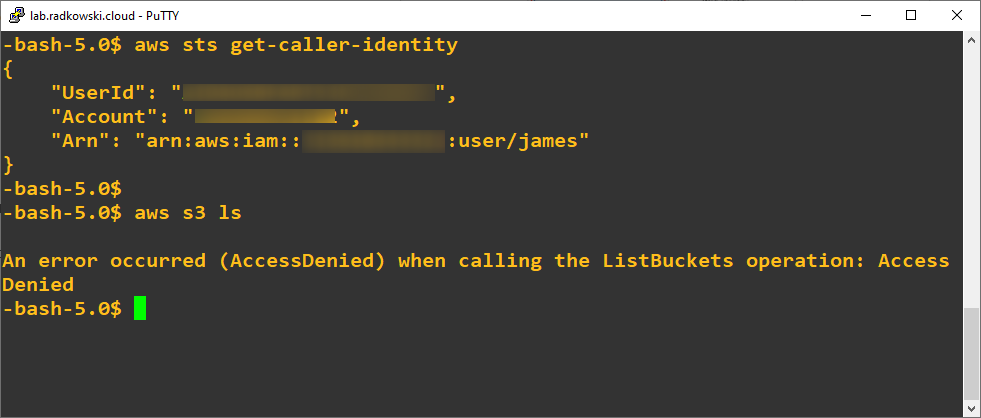
To confirm your current identity (user James), execute following command:
aws sts get-caller-identity
Next, try to list S3 buckets. Command will return AccessDenied as James is not allowed to perform this action.
19. Assume role
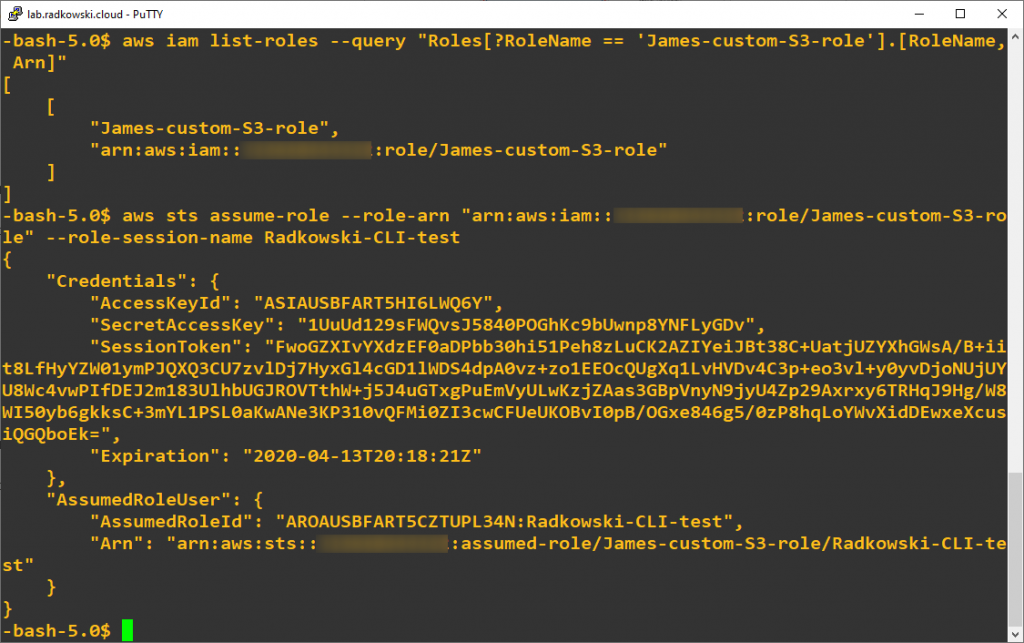
To discover role ARN (needed in next step), execute following command:
aws iam list-roles --query "Roles[?RoleName == 'James-custom-S3-role'].[RoleName, Arn]"
Role can be assumed, now:
aws sts assume-role --role-arn "arn:aws:iam::123456789012:role/James-custom-S3-role" --role-session-name Radkowski-CLI-test
Above command will return new temporary credentials:
- Access Key ID
- Secret Access Key
- Session Token
20. Check access
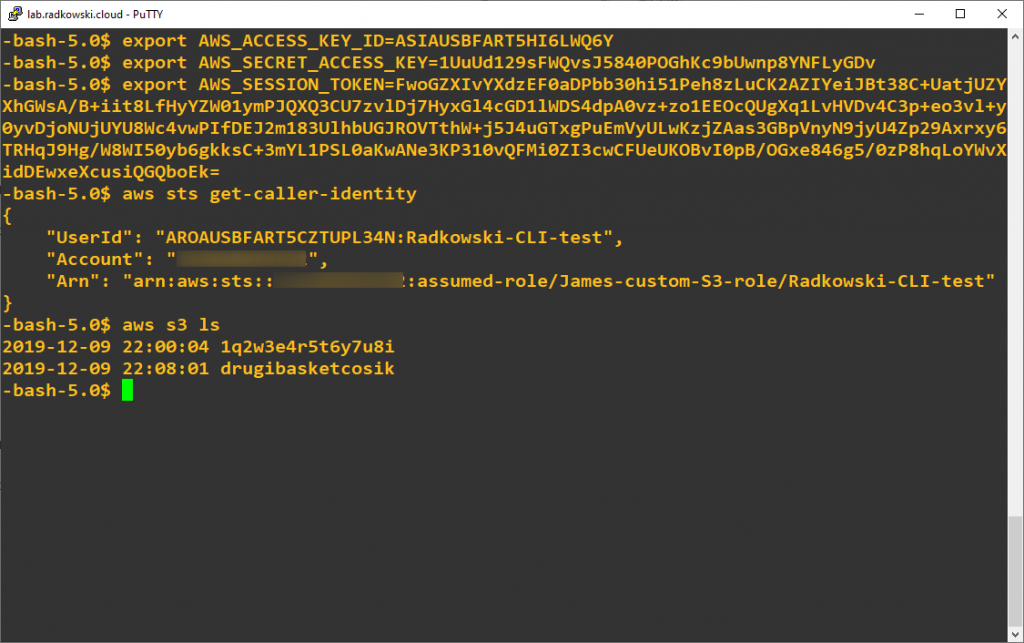
Once new credentials has been collected, export it using export command in bash (or simmilar procedure related to your shell).
Now you can again execute following command to check your identity. It should changed now to James-custom-S3-role
aws sts get-caller-identity
Execute aws s3 ls command to list buckets. This time command will return list of all configured S3 buckets.