MIT KERBEROS INSTALLATION
Description
Kerberos is a network authentication protocol. It is designed to provide strong authentication for client/server applications by using secret-key cryptography. A free implementation of this protocol is available from the Massachusetts Institute of Technology. Kerberos is available in many commercial products as well.
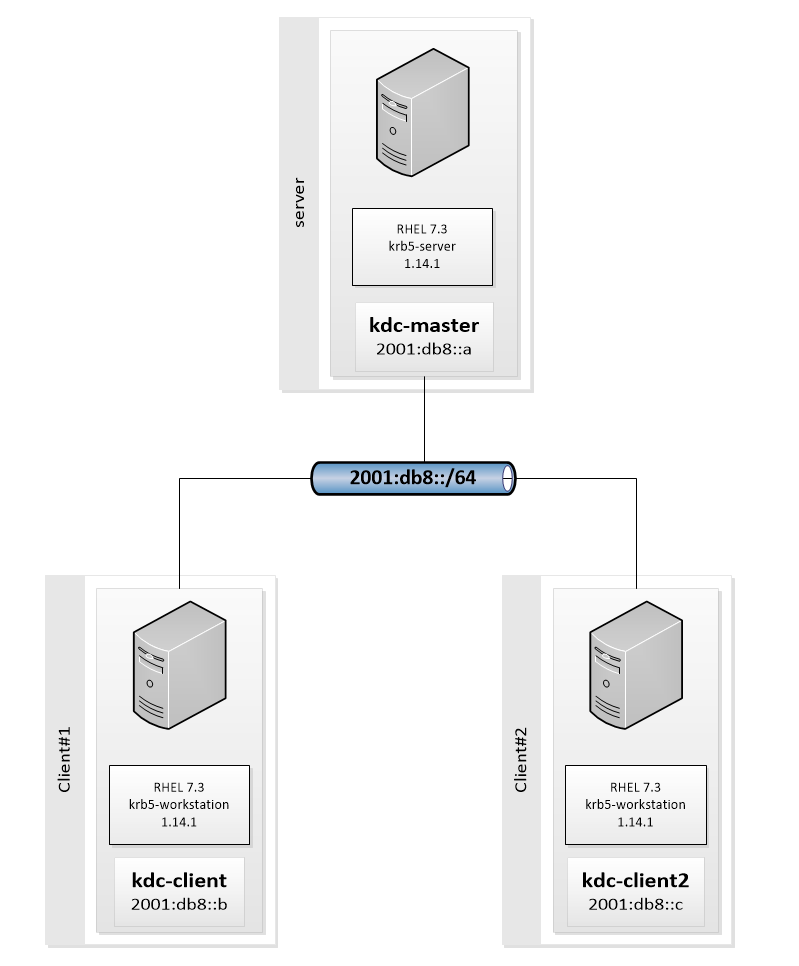
Lab Schema
Configs
1. Install packages
[radmin@kdc-master ~]$ sudo yum install krb5-server
Loaded plugins: product-id, search-disabled-repos, subscription-manager
This system is not registered to Red Hat Subscription Management. You can use subscription-manager to register.
Resolving Dependencies
--> Running transaction check
---> Package krb5-server.x86_64 0:1.14.1-26.el7 will be installed
--> Finished Dependency Resolution
Dependencies Resolved
================================================================================
Package Arch Version Repository Size
================================================================================
Installing:
krb5-server x86_64 1.14.1-26.el7 local 977 k
Transaction Summary
================================================================================
Install 1 Package
Total download size: 977 k
Installed size: 1.3 M
Is this ok [y/d/N]: y
Downloading packages:
Running transaction check
Running transaction test
Transaction test succeeded
Running transaction
Installing : krb5-server-1.14.1-26.el7.x86_64 1/1
Verifying : krb5-server-1.14.1-26.el7.x86_64 1/1
Installed:
krb5-server.x86_64 0:1.14.1-26.el7
Complete!
2. Edit Kerberos configuration file (/etc/krb5.conf)
[radmin@kdc-master ~]$ sudo vim /etc/krb5.conf
[radmin@kdc-master ~]$ cat /etc/krb5.conf
# Configuration snippets may be placed in this directory as well
includedir /etc/krb5.conf.d/
[logging]
default = FILE:/var/log/krb5libs.log
kdc = FILE:/var/log/krb5kdc.log
admin_server = FILE:/var/log/kadmind.log
[libdefaults]
dns_lookup_realm = false
ticket_lifetime = 24h
renew_lifetime = 7d
forwardable = true
rdns = false
default_realm = RADKOWSKI.PRO
default_ccache_name = KEYRING:persistent:%{uid}
[realms]
RADKOWSKI.PRO = {
kdc = kdc-master.radkowski.pro
admin_server = kdc-master.radkowski.pro
}
[domain_realm]
.radkowski.pro = RADKOWSKI.PRO
radkowski.pro = RADKOWSKI.PRO
3. Modify Kerberos ACL file
[radmin@kdc-master ~]$ sudo vim /var/kerberos/krb5kdc/kadm5.acl
[radmin@kdc-master ~]$ sudo cat /var/kerberos/krb5kdc/kadm5.acl
*/admin@RADKOWSKI.PRO *
4. Modify Kerberos V5 KDC configuration file:
[radmin@kdc-master ~]$ sudo vim /var/kerberos/krb5kdc/kdc.conf
[radmin@kdc-master ~]$ sudo cat /var/kerberos/krb5kdc/kdc.conf
[kdcdefaults]
kdc_ports = 88
kdc_tcp_ports = 88
[realms]
RADKOWSKI.PRO = {
#master_key_type = aes256-cts
acl_file = /var/kerberos/krb5kdc/kadm5.acl
dict_file = /usr/share/dict/words
admin_keytab = /var/kerberos/krb5kdc/kadm5.keytab
supported_enctypes = aes256-cts:normal aes128-cts:normal des3-hmac-sha1:normal arcfour-hmac:normal camellia256-cts:normal camellia128-cts:normal des-hmac-sha1:normal des-cbc-md5:normal des-cbc-crc:normal
}
5. Create new database and the stash file
[radmin@kdc-master ~]$ sudo kdb5_util create -s
Loading random data
Initializing database '/var/kerberos/krb5kdc/principal' for realm 'RADKOWSKI.PRO',
master key name 'K/M@RADKOWSKI.PRO'
You will be prompted for the database Master Password.
It is important that you NOT FORGET this password.
Enter KDC database master key:
Re-enter KDC database master key to verify:
6. Enable/Start/Check krbkdc and kadmin daemons
[radmin@kdc-master ~]$ sudo systemctl start krb5kdc
[radmin@kdc-master ~]$ sudo systemctl start kadmin
[radmin@kdc-master ~]$ sudo systemctl enable krb5kdc
Created symlink from /etc/systemd/system/multi-user.target.wants/krb5kdc.service to /usr/lib/systemd/system/krb5kdc.service.
[radmin@kdc-master ~]$ sudo systemctl enable kadmin
Created symlink from /etc/systemd/system/multi-user.target.wants/kadmin.service to /usr/lib/systemd/system/kadmin.service.
[radmin@kdc-master ~]$ sudo systemctl status krb5kdc
● krb5kdc.service - Kerberos 5 KDC
Loaded: loaded (/usr/lib/systemd/system/krb5kdc.service; enabled; vendor preset: disabled)
Active: active (running) since Fri 2017-06-09 21:45:59 BST; 22s ago
Main PID: 2757 (krb5kdc)
CGroup: /system.slice/krb5kdc.service
└─2757 /usr/sbin/krb5kdc -P /var/run/krb5kdc.pid
[radmin@kdc-master ~]$ sudo systemctl status kadmin
● kadmin.service - Kerberos 5 Password-changing and Administration
Loaded: loaded (/usr/lib/systemd/system/kadmin.service; enabled; vendor preset: disabled)
Active: active (running) since Fri 2017-06-09 21:46:04 BST; 22s ago
Main PID: 2766 (kadmind)
CGroup: /system.slice/kadmin.service
└─2766 /usr/sbin/kadmind -P /var/run/kadmind.pid
Principals Configuration
7. Add root/admin principals using kadmin.local
[radmin@kdc-master ~]$ sudo kadmin.local
Authenticating as principal root/admin@RADKOWSKI.PRO with password.
kadmin.local: addprinc root/admin
WARNING: no policy specified for root/admin@RADKOWSKI.PRO; defaulting to no policy
Enter password for principal "root/admin@RADKOWSKI.PRO":
Re-enter password for principal "root/admin@RADKOWSKI.PRO":
Principal "root/admin@RADKOWSKI.PRO" created.
kadmin.local: quit
8. Add users (tom, jane) principals
[radmin@kdc-master ~]$ sudo yum install krb5-workstation
Installed:
krb5-workstation.x86_64 0:1.14.1-26.el7
Complete!
[radmin@kdc-master ~]$ sudo kadmin
Authenticating as principal root/admin@RADKOWSKI.PRO with password.
Password for root/admin@RADKOWSKI.PRO:
kadmin: addprinc tom
WARNING: no policy specified for tom@RADKOWSKI.PRO; defaulting to no policy
Enter password for principal "tom@RADKOWSKI.PRO":
Re-enter password for principal "tom@RADKOWSKI.PRO":
Principal "tom@RADKOWSKI.PRO" created.
kadmin: addprinc jane
WARNING: no policy specified for jane@RADKOWSKI.PRO; defaulting to no policy
Enter password for principal "jane@RADKOWSKI.PRO":
Re-enter password for principal "jane@RADKOWSKI.PRO":
Principal "jane@RADKOWSKI.PRO" created.
kadmin: listprincs
K/M@RADKOWSKI.PRO
jane@RADKOWSKI.PRO
kadmin/admin@RADKOWSKI.PRO
kadmin/changepw@RADKOWSKI.PRO
kadmin/radkowski.pro@RADKOWSKI.PRO
kiprop/radkowski.pro@RADKOWSKI.PRO
krbtgt/RADKOWSKI.PRO@RADKOWSKI.PRO
root/admin@RADKOWSKI.PRO
tom@RADKOWSKI.PRO
kadmin: quit
Clients config
9. Install packages and check connection to kdc-master
[radmin@kdc-client ~]$ sudo yum install krb5-workstation pam_krb5
Loaded plugins: product-id, search-disabled-repos, subscription-manager
This system is not registered to Red Hat Subscription Management. You can use subscription-manager to register.
Installing : krb5-workstation-1.14.1-26.el7.x86_64 1/2
Installing : pam_krb5-2.4.8-6.el7.x86_64 2/2
Verifying : pam_krb5-2.4.8-6.el7.x86_64 1/2
Verifying : krb5-workstation-1.14.1-26.el7.x86_64 2/2
Installed:
krb5-workstation.x86_64 0:1.14.1-26.el7 pam_krb5.x86_64 0:2.4.8-6.el7
Complete!
[radmin@kdc-client ~]$ ping6 -c3 kdc-master.radkowski.pro
PING kdc-master.radkowski.pro(kdc-master.radkowski.pro (2001:db8::a)) 56 data bytes
64 bytes from kdc-master.radkowski.pro (2001:db8::a): icmp_seq=1 ttl=64 time=0.401 ms
64 bytes from kdc-master.radkowski.pro (2001:db8::a): icmp_seq=2 ttl=64 time=0.387 ms
64 bytes from kdc-master.radkowski.pro (2001:db8::a): icmp_seq=3 ttl=64 time=0.374 ms
--- kdc-master.radkowski.pro ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2000ms
rtt min/avg/max/mdev = 0.374/0.387/0.401/0.019 ms
10. Edit Kerberos configuration file (/etc/krb5.conf)
[radmin@kdc-client ~]$ sudo vim /etc/krb5.conf
[radmin@kdc-client ~]$ cat /etc/krb5.conf
includedir /etc/krb5.conf.d/
[logging]
default = FILE:/var/log/krb5libs.log
kdc = FILE:/var/log/krb5kdc.log
admin_server = FILE:/var/log/kadmind.log
[libdefaults]
dns_lookup_realm = false
ticket_lifetime = 24h
renew_lifetime = 7d
forwardable = true
rdns = false
default_realm = RADKOWSKI.PRO
default_ccache_name = KEYRING:persistent:%{uid}
[realms]
RADKOWSKI.PRO = {
kdc = kdc-master.radkowski.pro
admin_server = kdc-master.radkowski.pro
}
[domain_realm]
.radkowski.pro = RADKOWSKI.PRO
radkowski.pro = RADKOWSKI.PRO
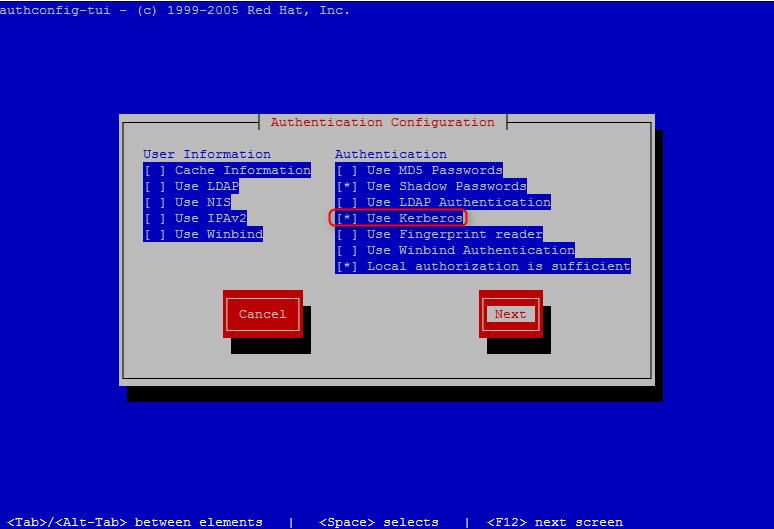
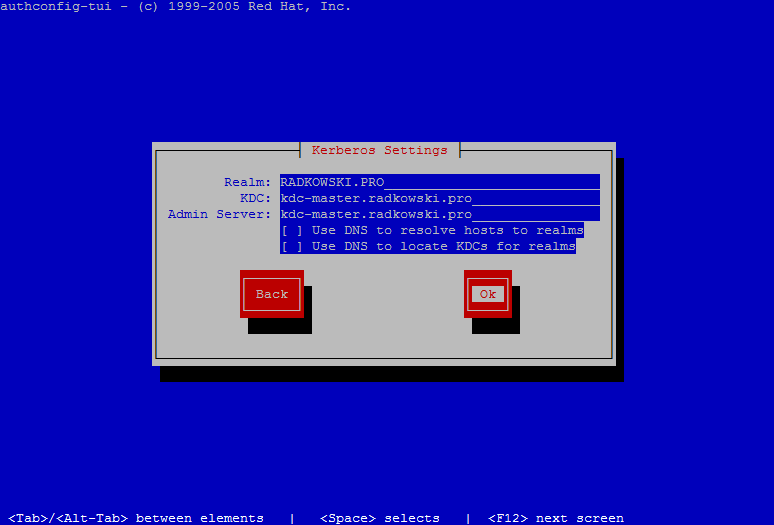
11. Reconfigure system authentication resources
radmin@kdc-client ~]sudo authconfig --enablemkhomedir --update
radmin@kdc-client ~] sudo authconfig-tui
12. Modify ssh configuration
[radmin@kdc-client ~]$ cat /etc/ssh/ssh_config | grep GSSAPI
GSSAPIAuthentication yes
GSSAPIDelegateCredentials yes
# GSSAPIKeyExchange no
# GSSAPITrustDNS no
GSSAPIAuthentication yes
[radmin@kdc-client ~]$
13. Create host principals
[radmin@kdc-client ~]$ sudo kadmin
Authenticating as principal root/admin@RADKOWSKI.PRO with password.
Password for root/admin@RADKOWSKI.PRO:
kadmin: addprinc -randkey host/kdc-client.radkowski.pro
WARNING: no policy specified for host/kdc-client.radkowski.pro@RADKOWSKI.PRO; defaulting to no policy
Principal "host/kdc-client.radkowski.pro@RADKOWSKI.PRO" created.
kadmin: ktadd host/kdc-client.radkowski.pro
Entry for principal host/kdc-client.radkowski.pro with kvno 2, encryption type aes256-cts-hmac-sha1-96 added to keytab FILE:/etc/krb5.keytab.
Entry for principal host/kdc-client.radkowski.pro with kvno 2, encryption type aes128-cts-hmac-sha1-96 added to keytab FILE:/etc/krb5.keytab.
Entry for principal host/kdc-client.radkowski.pro with kvno 2, encryption type des3-cbc-sha1 added to keytab FILE:/etc/krb5.keytab.
Entry for principal host/kdc-client.radkowski.pro with kvno 2, encryption type arcfour-hmac added to keytab FILE:/etc/krb5.keytab.
Entry for principal host/kdc-client.radkowski.pro with kvno 2, encryption type camellia256-cts-cmac added to keytab FILE:/etc/krb5.keytab.
Entry for principal host/kdc-client.radkowski.pro with kvno 2, encryption type camellia128-cts-cmac added to keytab FILE:/etc/krb5.keytab.
Entry for principal host/kdc-client.radkowski.pro with kvno 2, encryption type des-hmac-sha1 added to keytab FILE:/etc/krb5.keytab.
Entry for principal host/kdc-client.radkowski.pro with kvno 2, encryption type des-cbc-md5 added to keytab FILE:/etc/krb5.keytab.
kadmin: quit