MIT KERBEROS M/S REPLICATION
Description
kprop is used to securely propagate a Kerberos V5 database dump file from the master Kerberos server to a slave Kerberos server, which is specified by slave_host. The dump file must be created by kdb5_util.
Lab Schema
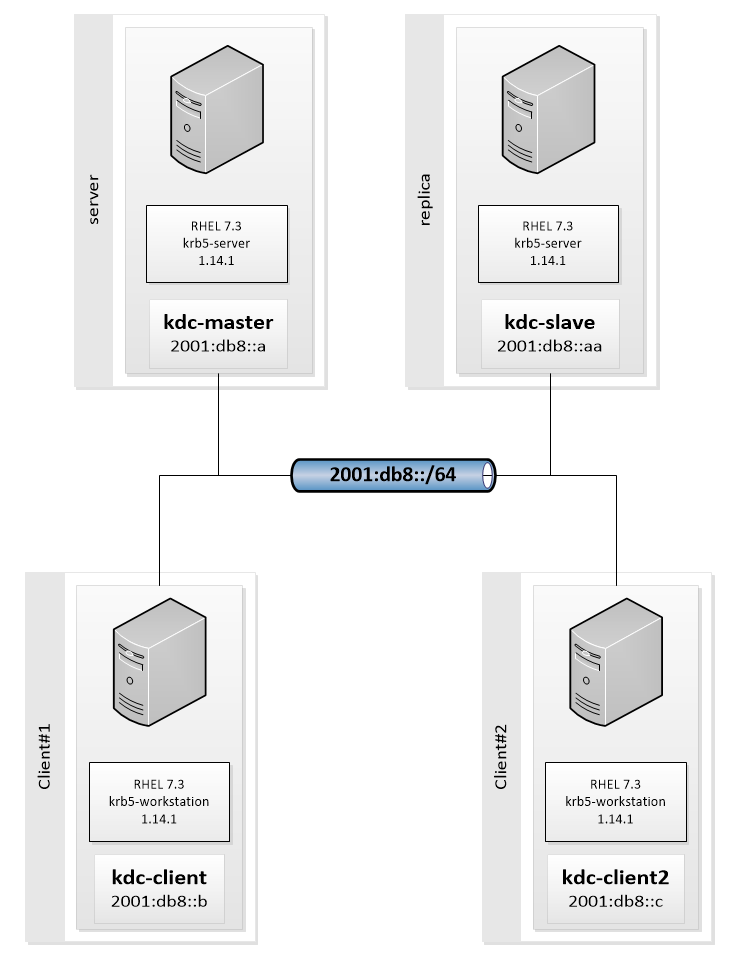
Preconfiguration
Another configuration must be prepared before you will continue. Click button on the right to jump into
MIT KERBEROS INSTALLATION HOWTO
Configs
Modify kerberos configuration file
[radmin@kdc-master ~]$ sudo vim /etc/krb5.conf
includedir /etc/krb5.conf.d/
[logging]
default = FILE:/var/log/krb5libs.log
kdc = FILE:/var/log/krb5kdc.log
admin_server = FILE:/var/log/kadmind.log
[libdefaults]
dns_lookup_realm = false
ticket_lifetime = 24h
renew_lifetime = 7d
forwardable = true
rdns = false
default_realm = RADKOWSKI.PRO
default_ccache_name = KEYRING:persistent:%{uid}
dns_lookup_kdc = false
[realms]
RADKOWSKI.PRO = {
kdc = kdc-master.radkowski.pro
kdc = kdc-slave.radkowski.pro
master_kdc = kdc-master.radkowski.pro
admin_server = kdc-master.radkowski.pro
}
[domain_realm]
.radkowski.pro = RADKOWSKI.PRO
radkowski.pro = RADKOWSKI.PRO
2. Create kdc-master host principals
[radmin@kdc-master ~]$ sudo kadmin
Authenticating as principal root/admin@RADKOWSKI.PRO with password.
Password for root/admin@RADKOWSKI.PRO:
kadmin: addprinc -randkey host/kdc-master.radkowski.pro
WARNING: no policy specified for host/kdc-client.radkowski.pro@RADKOWSKI.PRO; defaulting to no policy
Principal “host/kdc-master.radkowski.pro@RADKOWSKI.PRO” created.
kadmin: ktadd host/kdc-master.radkowski.pro
Entry for principal host/kdc-master.radkowski.pro with kvno 2, encryption type aes256-cts-hmac-sha1-96 added to keytab FILE:/etc/krb5.keytab.
(...)
kadmin: quit
3. Create sync script
[radmin@kdc-master ~]$ sudo cat /opt/scripts/sync_krb
#!/bin/bash
kdb5_util dump /var/kerberos/krb5kdc/slave_dump
kprop -d -f /var/kerberos/krb5kdc/slave_dump kdc-slave.radkowski.pro
4. Install packages on kdc-slave
[radmin@kdc-slave ~]$ sudo yum install krb5-server krb5-workstation
Loaded plugins: product-id, search-disabled-repos, subscription-manager
This system is not registered to Red Hat Subscription Management. You can use subscription-manager to register.
Resolving Dependencies
–> Running transaction check
—> Package krb5-server.x86_64 0:1.14.1-26.el7 will be installed
–> Finished Dependency Resolution
Dependencies Resolved
(...)
Installed:
krb5-server.x86_64 0:1.14.1-26.el7
krb5-workstation-1.14.1-26.el7
Complete!
5. Copy config files from kdc-master to kdc-slave
[radmin@kdc-slave ~]$ sudo scp root@kdc-master:/etc/krb5.conf /etc/krb5.conf
root@kdc-master's password:
krb5.conf 100% 699 0.7KB/s 00:00
[radmin@kdc-slave ~]$ sudo scp root@kdc-master:/var/kerberos/krb5kdc/kdc.conf /var/kerberos/krb5kdc/kdc.conf
root@kdc-master's password:
kdc.conf 100% 871 KB/s 00:00
[radmin@kdc-slave ~]$ sudo restorecon /etc/krb5.conf
[radmin@kdc-slave ~]$ sudo restorecon /var/kerberos/krb5kdc/kdc.conf
6. Create kpropd acl file
[radmin@kdc-slave ~]$ sudo cat /var/kerberos/krb5kdc/kpropd.acl
host/kdc-master.radkowski.pro@RADKOWSKI.PRO
[radmin@kdc-slave ~]$
7. Create kdc-slave host principals
[radmin@kdc-slave ~]$ sudo kadmin
Authenticating as principal root/admin@RADKOWSKI.PRO with password.
Password for root/admin@RADKOWSKI.PRO:
kadmin: addprinc -randkey host/kdc-slave.radkowski.pro
WARNING: no policy specified for host/kdc-client.radkowski.pro@RADKOWSKI.PRO; defaulting to no policy
Principal “host/kdc-slave.radkowski.pro@RADKOWSKI.PRO” created.
kadmin: ktadd host/kdc-slave.radkowski.pro
Entry for principal host/kdc-slave.radkowski.pro with kvno 2, encryption type aes256-cts-hmac-sha1-96 added to keytab FILE:/etc/krb5.keytab.
(…)
kadmin: quit
8. Create new database and the stash file on kdc-slave
[radmin@kdc-slave ~]$ sudo kdb5_util create -s
Loading random data
Initializing database ‘/var/kerberos/krb5kdc/principal’ for realm ‘RADKOWSKI.PRO’,
master key name ‘K/M@RADKOWSKI.PRO’
You will be prompted for the database Master Password.
It is important that you NOT FORGET this password.
Enter KDC database master key:
Re-enter KDC database master key to verify:
9. Start/enable KDC server and kprop daemon
[radmin@kdc-slave ~]$ sudo systemctl start krb5kdc
[radmin@kdc-slave ~]$ sudo systemctl enable krb5kdc
[radmin@kdc-slave ~]$ sudo systemctl start kprop
[radmin@kdc-slave ~]$ sudo systemctl enable kprop
10. Sync data using sync_krb script
[radmin@kdc-master ~]$ sudo /opt/scripts/sync_krb
12280 bytes sent.
Database propagation to kdc-slave.radkowski.pro: SUCCEEDED
[radmin@kdc-master ~]$
11. Add script to the crontab. Sync script will be executed every five minutes
[radmin@kdc-master etc]$ sudo cat /etc/crontab
SHELL=/bin/bash
PATH=/sbin:/bin:/usr/sbin:/usr/bin
MAILTO=root
*/5 * * * * /opt/script/sync_krb
[radmin@kdc-master etc]$ sudo systemctl restart crond
Clients config
12. Update client kerberos config file
[radmin@kdc-client ~]$ sudo vim /etc/krb5.conf
includedir /etc/krb5.conf.d/
[logging]
default = FILE:/var/log/krb5libs.log
kdc = FILE:/var/log/krb5kdc.log
admin_server = FILE:/var/log/kadmind.log
[libdefaults]
dns_lookup_realm = false
ticket_lifetime = 24h
renew_lifetime = 7d
forwardable = true
rdns = false
default_realm = RADKOWSKI.PRO
default_ccache_name = KEYRING:persistent:%{uid}
dns_lookup_kdc = false
[realms]
RADKOWSKI.PRO = {
kdc = kdc-master.radkowski.pro
kdc = kdc-slave.radkowski.pro
master_kdc = kdc-master.radkowski.pro
admin_server = kdc-master.radkowski.pro
}
[domain_realm]
.radkowski.pro = RADKOWSKI.PRO
radkowski.pro = RADKOWSKI.PRO
[radmin@kdc-client ~]$ sudo authconfig --update
